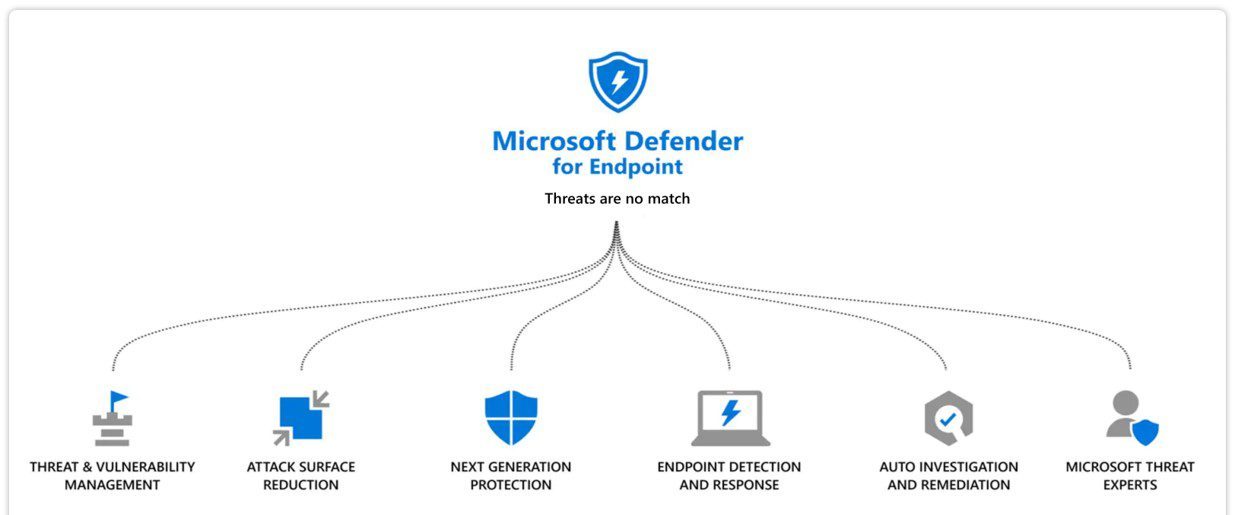
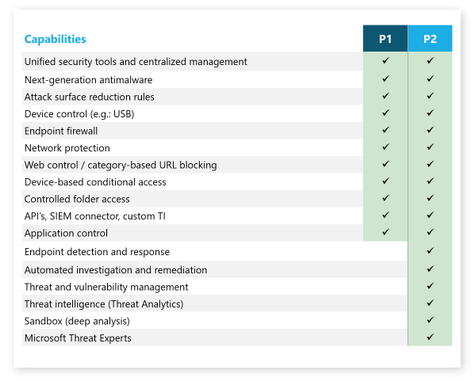
Whizlabs - 🛡️ Microsoft Defender for Endpoint: An overview 🛡️ 🔍 In today's digital world, the volume and complexity of cybersecurity threats and attacks are continuously increasing. 💪 🔒 Endpoints, such as

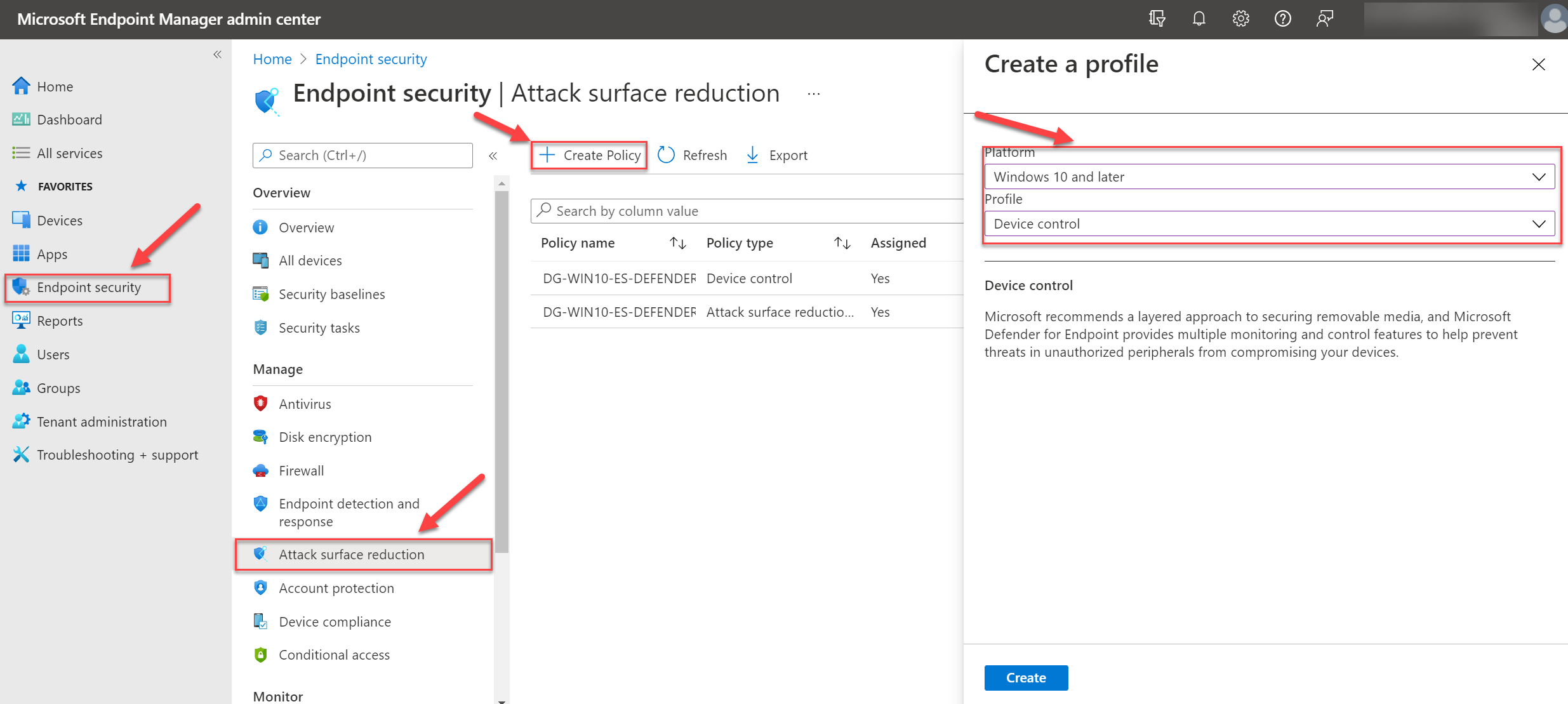
Deploy and manage device control in Microsoft Defender for Endpoint with Group Policy - Microsoft Defender for Endpoint | Microsoft Learn
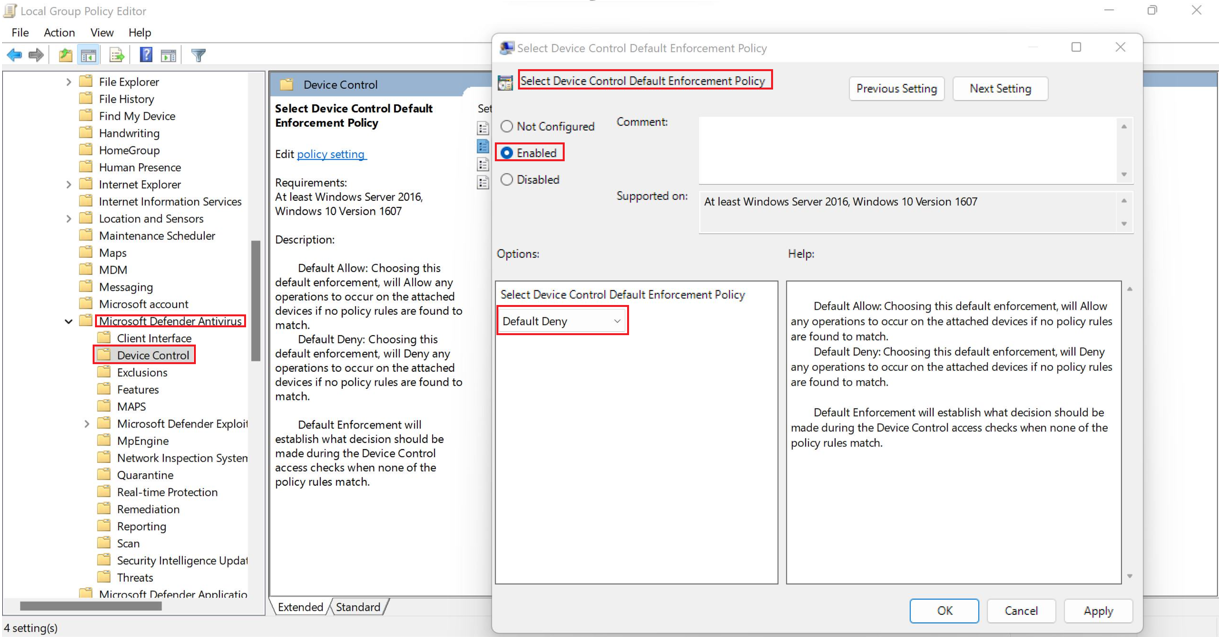
Deploy and manage device control in Microsoft Defender for Endpoint with Group Policy - Microsoft Defender for Endpoint | Microsoft Learn

Microsoft Defender for Endpoint: Key Configurations and Best Practices (2/2) – Modern Device Management

PART 2 - Deploy Endpoint Security policies to Linux Servers via Intune with Security Settings Management
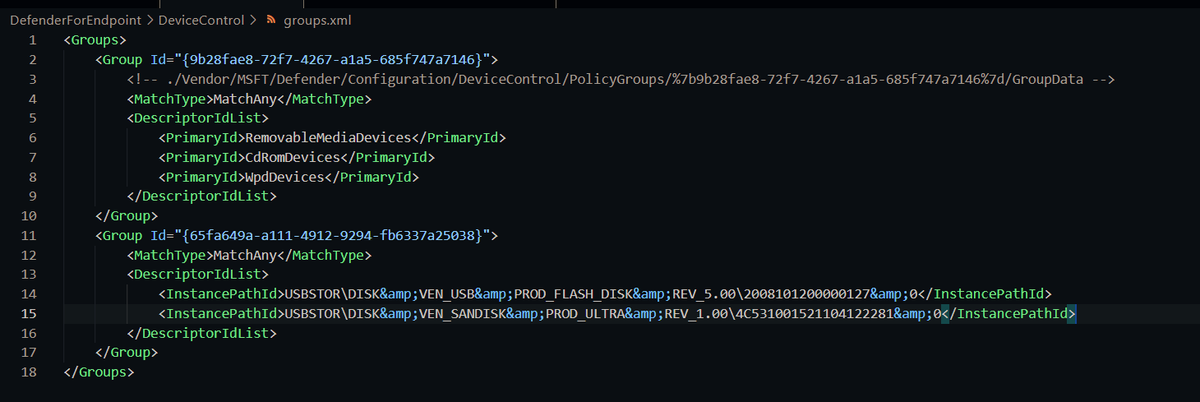
GitHub - microsoft/mdatp-devicecontrol: Microsoft Defender for Endpoint Device Control tools, samples, and resources.
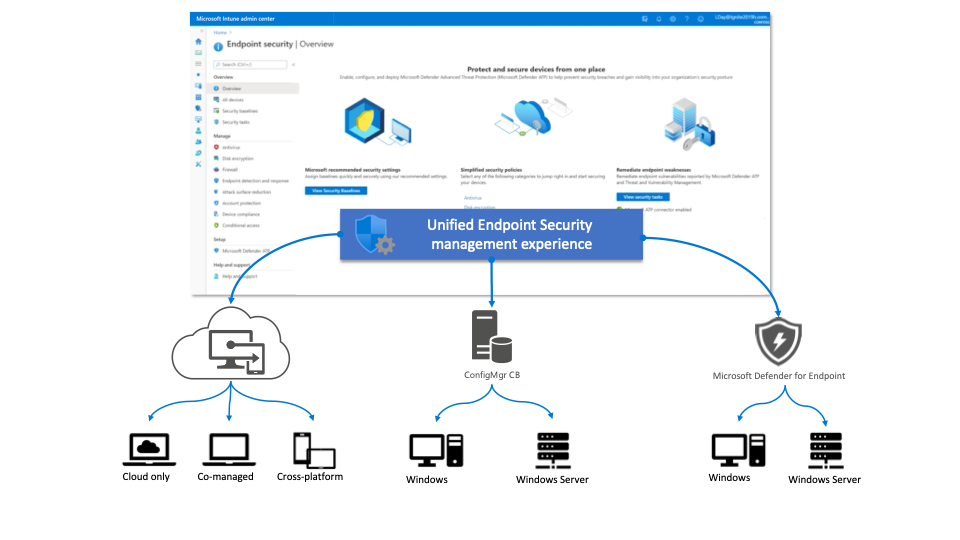
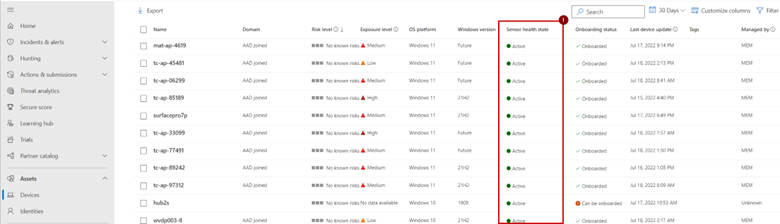
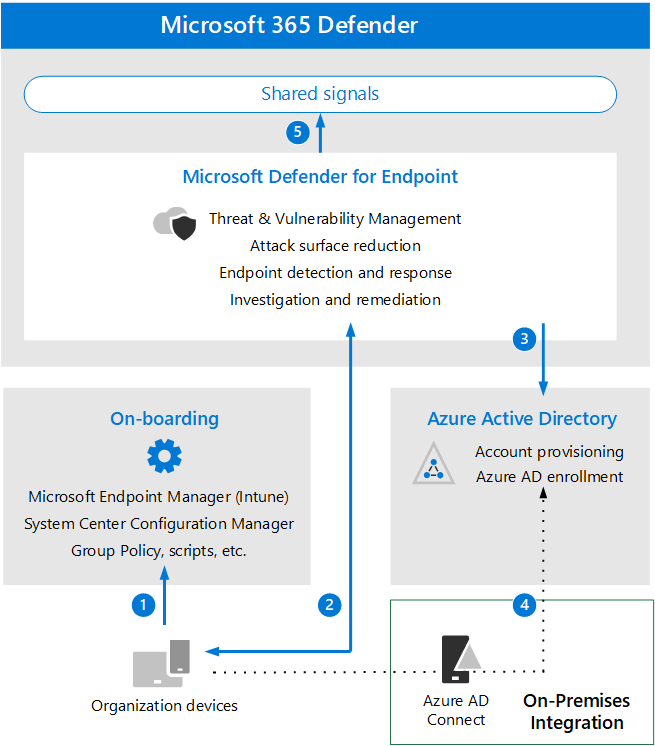
How to enroll device to Microsoft Defender for Endpoint and how does it work (1/2)? – Modern Device Management
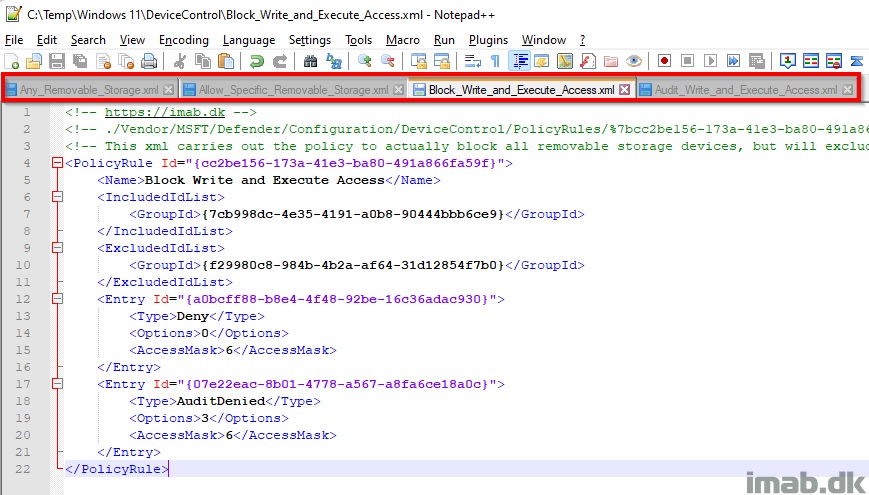
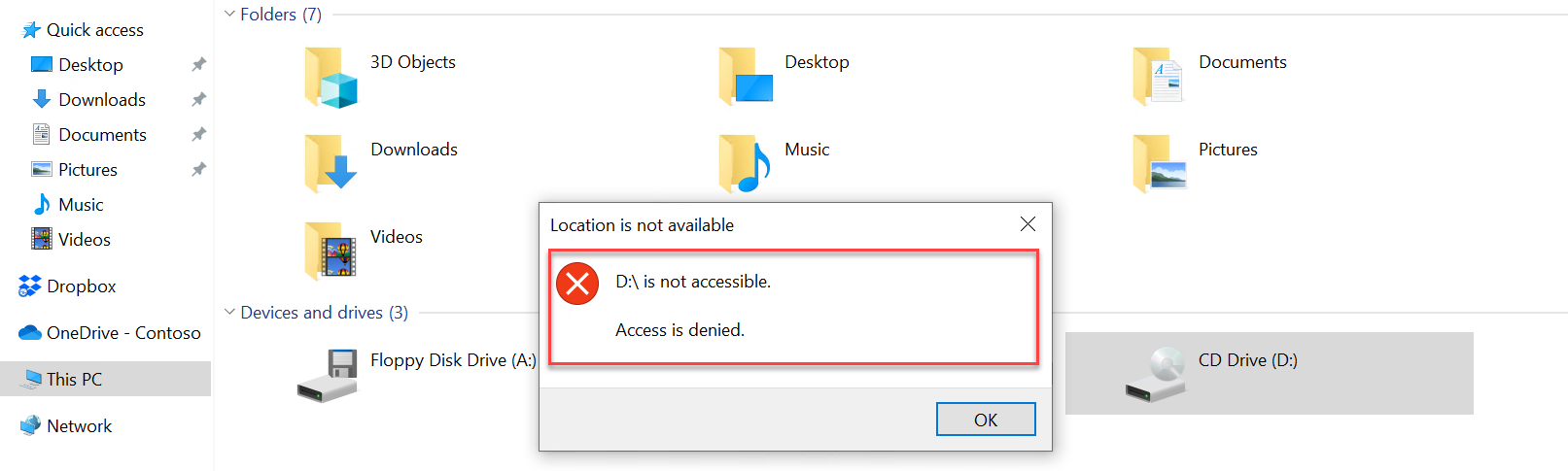
Prevent Write and Execute access to non-approved removable storage using Device Control and Microsoft Intune – imab.dk
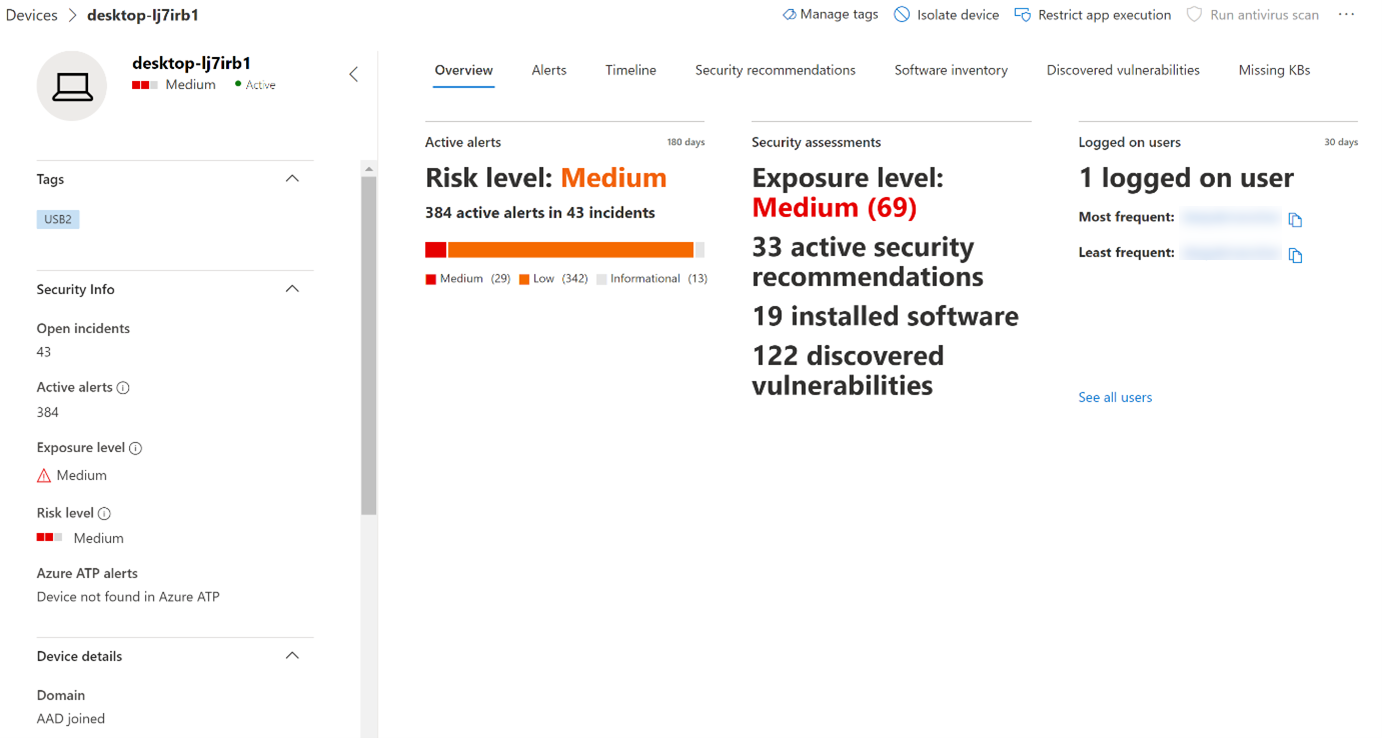
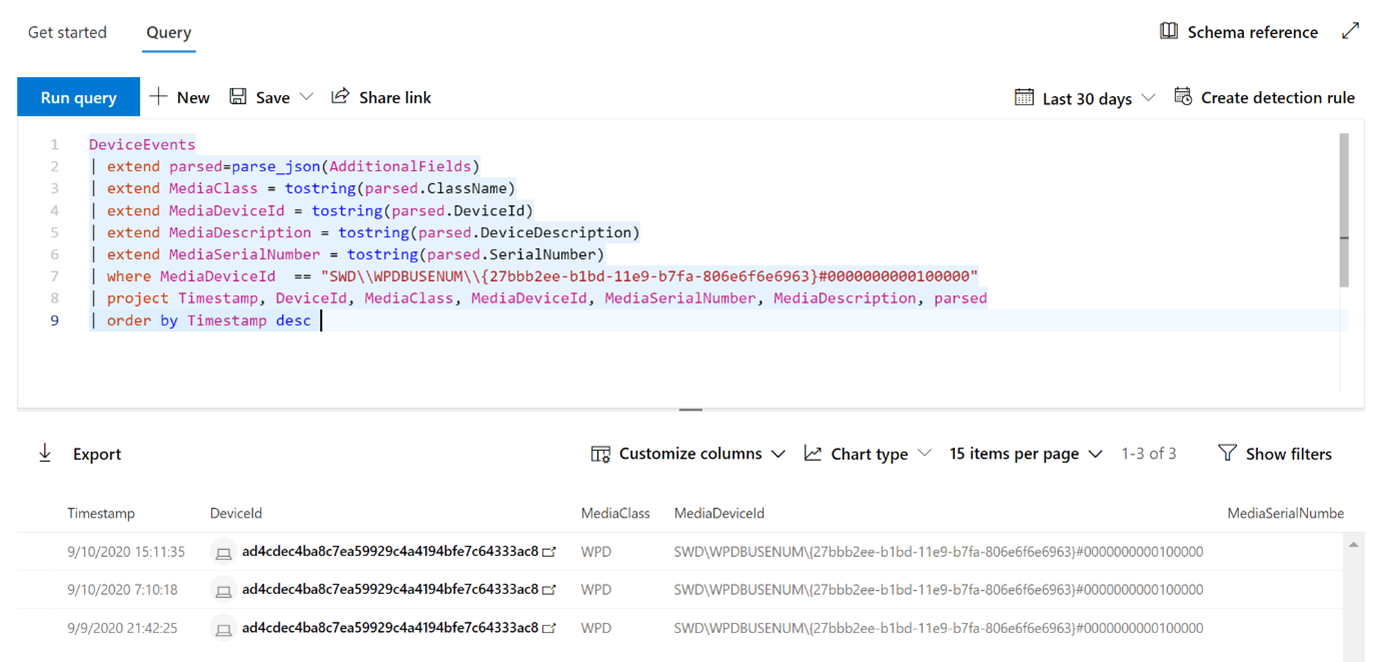
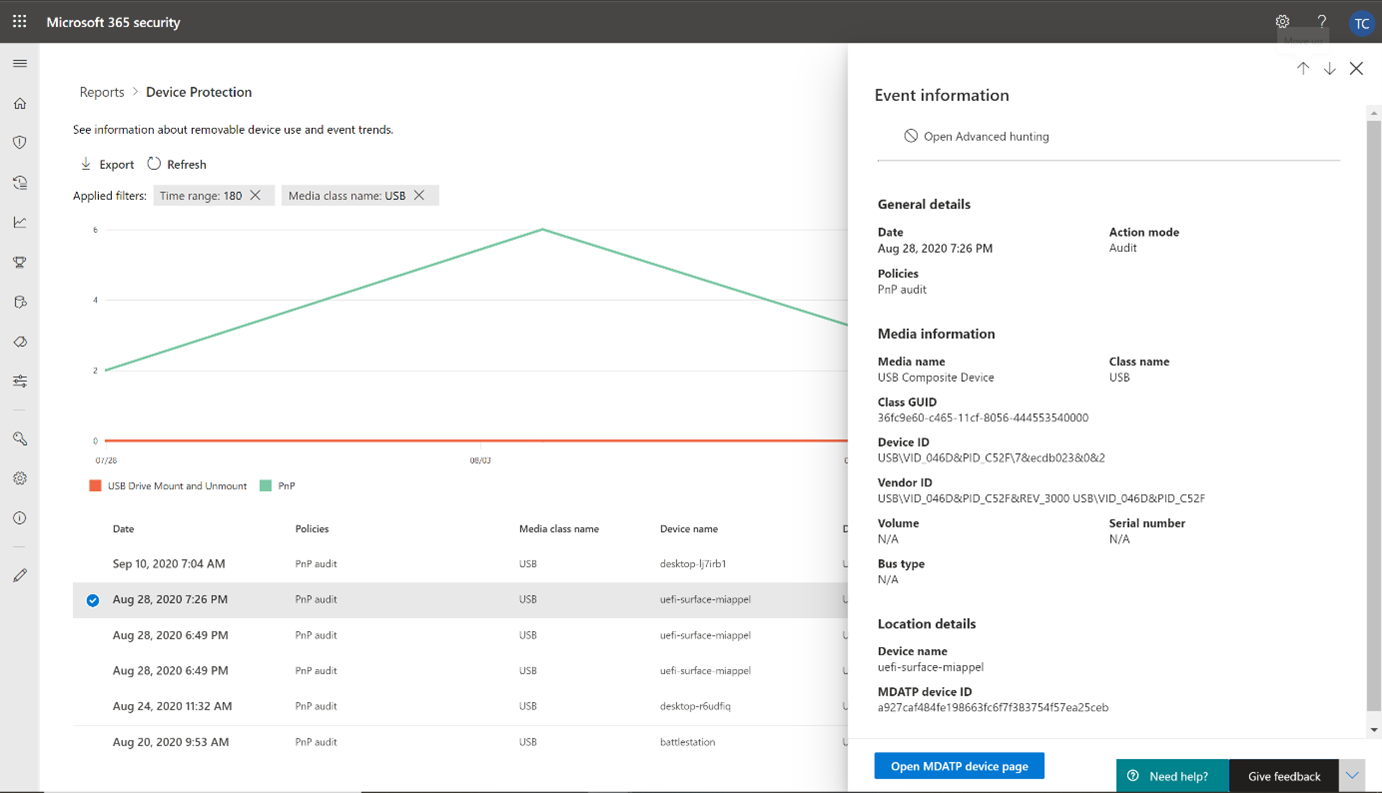
View device control events and information in Microsoft Defender for Endpoint - Microsoft Defender for Endpoint | Microsoft Learn